On May 4th, 2017 I discovered and privately reported a recipient spoofing vulnerability in Google Inbox. I noticed that the composition box always hid the email addresses of named recipients without providing a way to inspect the actual email address, and figured out how to abuse this with mailto: links containing named recipients.
The link mailto:”support@paypal.com”<scam@phisher.example> shows up as “support@paypal.com” in the Google Inbox composition window, visually identical to any email actually sent to PayPal.
In order to exploit this vulnerability, the target user only needs to click on a malicious mailto: link. It can also be triggered by clicking on a direct link to Inbox’s mailto: handler page, as shown in this example exploit link.
This vulnerability was still unfixed in all Google Inbox apps as of May 4th, 2018, a year after private disclosure.
Update: This vulnerability has been fixed in the Google Inbox webapp as of May 18, 2018. The Android app still remains vulnerable.
The recipient “support@paypal.com” being spoofed in the Google Inbox composition window. The actual recipient is “scam@phisher.example”.
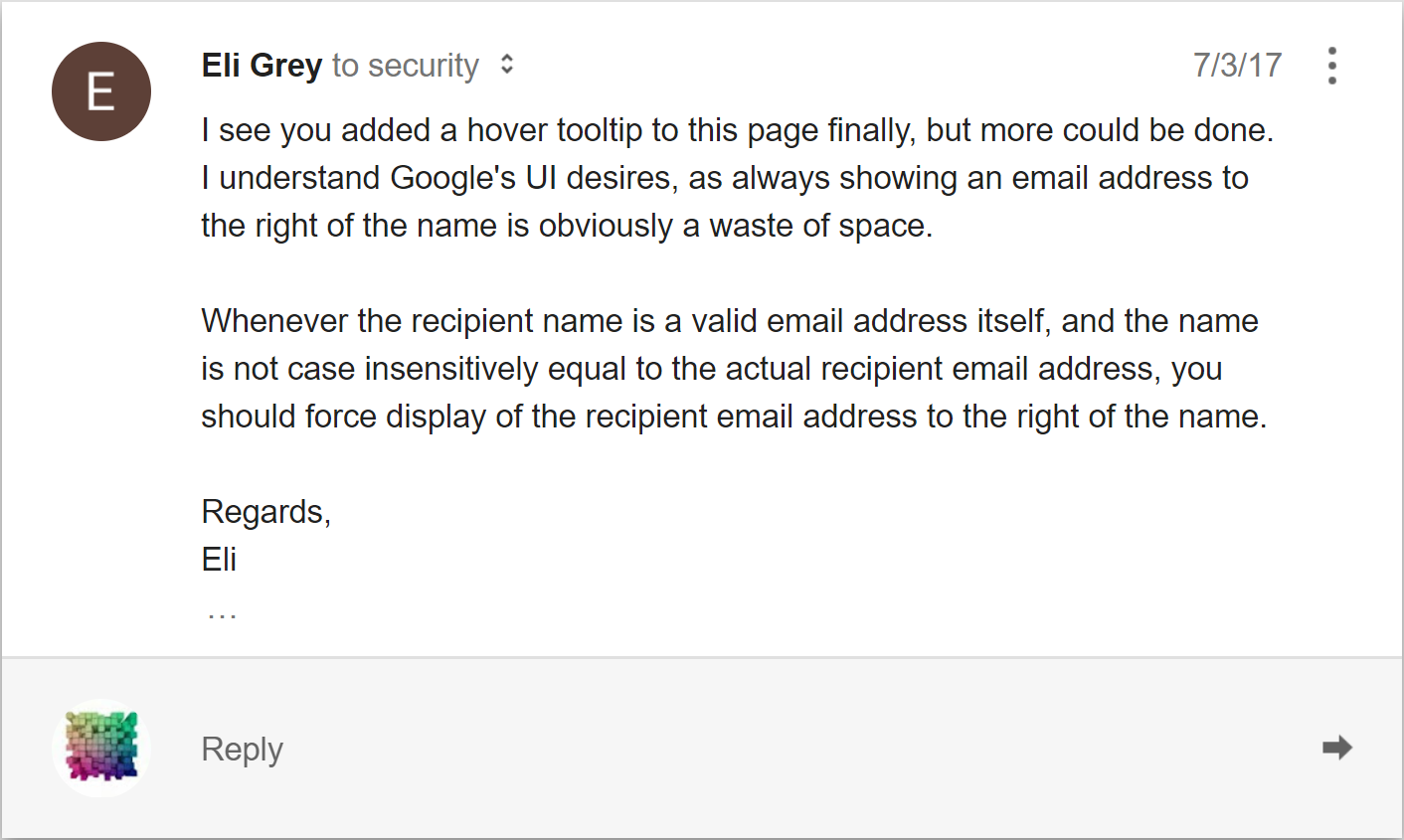
On July 3rd, 2017 I noticed that Google had added hover tooltips to this field in Inbox, which made it possible for users to manually confirm the recipient email address. The default presentation of the email address was still vulnerable to spoofing, so I sent another email to Google.
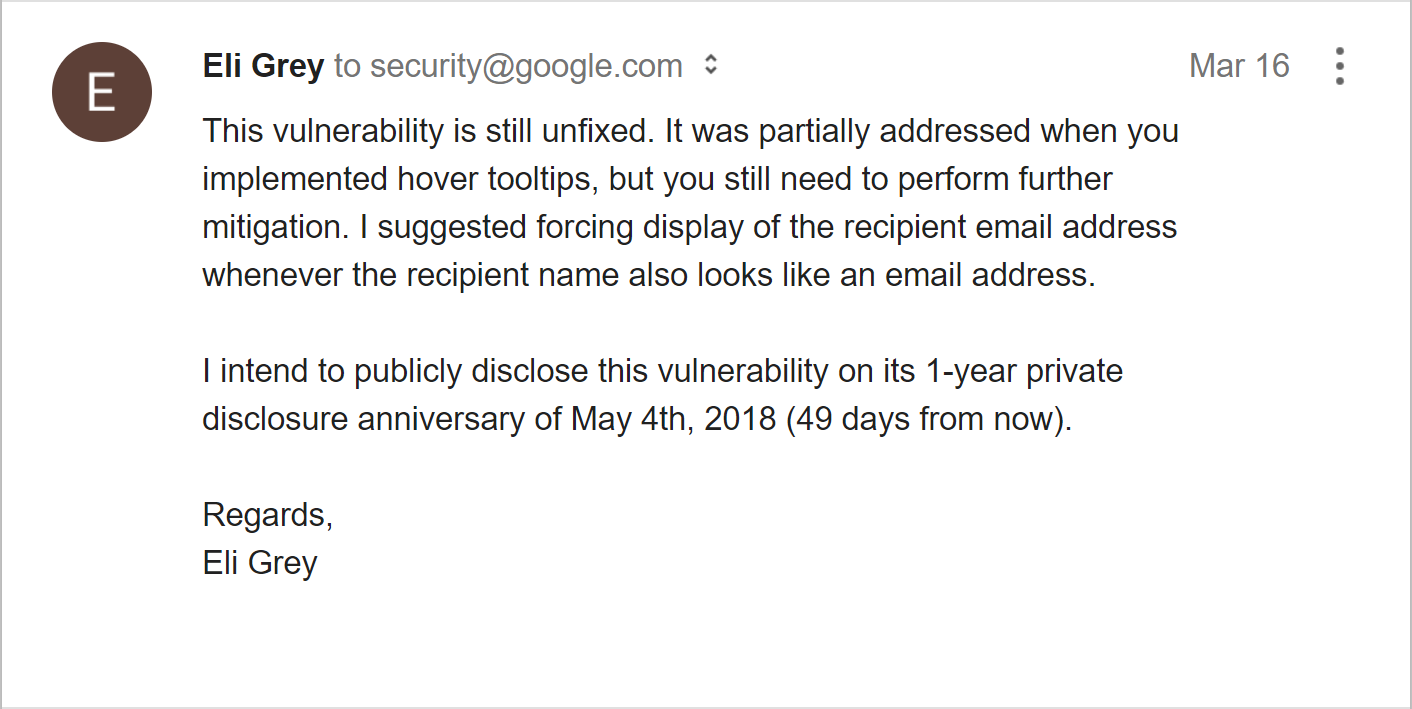
I received no response for over 8 months, so I sent yet another email on March 16th, 2018.
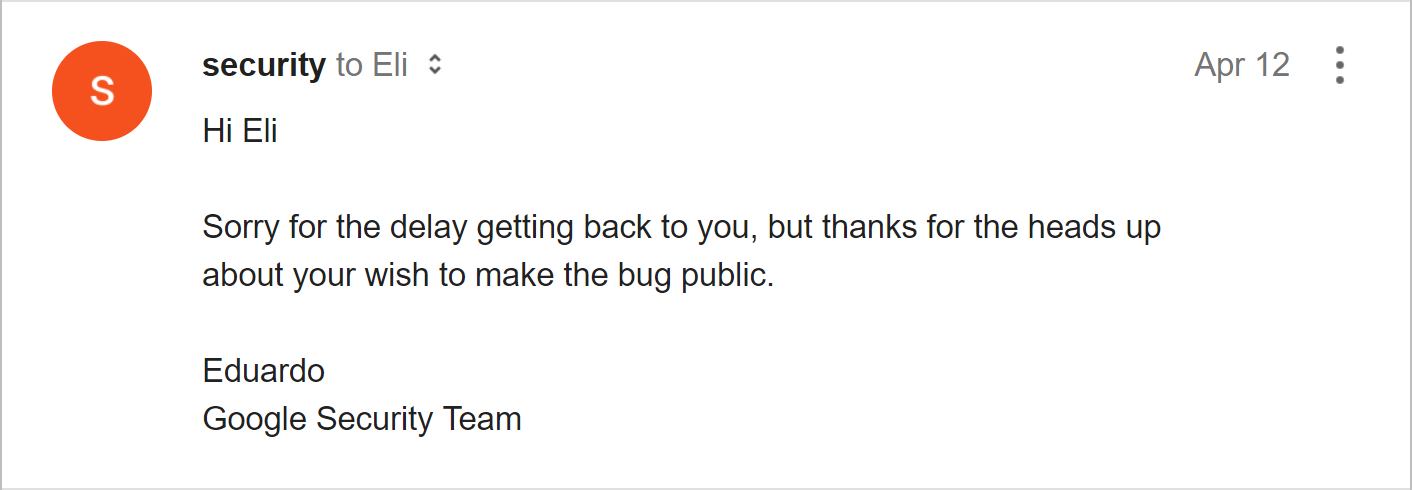
Nine months after sending my emails I received this response, which doesn’t lead me to believe that Google is serious about fixing this vulnerability.
[…] about the error led to a heated discussion that shed light on another vulnerability in Gmail, which allows you to replace the recipient’s email address. The problem was fixed in the Gmail web version, but […]